
go:Identity - The IAG Appliance
go:Identity is the preconfigured identity management software that can be deployed extremely quickly for user administration and administration of access rights.
With its standards and best practice functions, go:Identity finally enables Identity Management and Access Management (IAM - Identity Access Management) and Identity Access Governance (IAG) for companies of all sizes.
More than 50 out-of-the-box connectors for the connection to and integration of external target systems and databases exist and can be flexibly configured.
Because of its quick implementation, with automated user, access and role management, go:Identity helps increase security and reduce costs in the company. Compliance requirements are met and user friendliness is guaranteed. The perfect Identity Manager Tool.
We can implement a typical IDM project, involving MS Active Directory® and synchronization with an HR data source, with an external effort of only 10 days (more information on this below).
Together with the optional go:Identity Secure Access Module, go:Identity offers a comprehensive Identity and Access Management solution.
Resources:
Click here for a quick video about go:Identity:
Success Stories
Why use a preconfigured solution like go:Identity?
How can you still automate standard use cases cost-effectively and without much effort?
go:Identity is up and running faster than more traditional Identity & Access Management solutions for the same use cases. It includes features like user provisioning and de-provisioning, user self-service and approval workflows, just to name a few.
Projects with conventional IDM solutions
- Component selection
- Process analysis
- IDM best-practice definitions
- Design of basic processes
- Development
- Software QS
- Training
- High implementation cost
- Long project cycles
- Less to none standardisation
go:Identity projects
- Implementaion and Customizing
- Use Cases Tests
- Introduction / Training
+ prompt implementation
+ proven processes
+ secure standards
+ compliance without effort
Minimal project risk withgo:Identity
The out-of-the-box approach significantly reduces project risk in our projects. Thanks to the built-in best practice, the processes and functions have already proven their suitability.
Instead of long-running projects with imprecise, slowly emerging results, go:Identity immediately gives you an almost-finished system. It only needs to be configured instead of programmed.
A typical project
IDM projects are not rocket science and do not have to be as complex as it is often portrayed.
Right out of the box, go:Identity offers the exact functions that are important for identity management and that have already proven themselves hundreds of times in practice.
We can realize a complete IDM project, e.g.
- with Active Directory® as the target system and
- connection of a HR data source
in collaboration with our customers, with an external effort of
just 10 days
from the first requirements workshop to the go-live.
Stay flexible with go:Identity
The approach is important
Think in phases so you can start the 1st phase with goals that will quickly bring the greatest benefit, e.g. in the form of reduced effort and increased security.
Additional features can be added in later phases:
-
other target systems (e.g. SAP, Office365, etc.)
-
further automation other scenarios such as access management
-
customer-specific extensions of all kinds
-
and much more.
You can be confident that go:Identity is always prepared for future requirements.
Typical Use Cases for Identity Management
- Use Case "Automation"
- Use Case "Manage Fileshare Access"
- Use Case "Cloud and Azure AD"
- Use Case "Compliance Audit"

Challenge:
Does high risk = high cost?
A distribution system operator had to provide secure access to critical infrastructure. Managing accounts and maintaining access was error-prone and cumbersome.

Solution:
Automation reduces risk and cost
go:Identity automated account and entitlement management by standardizing the processes. Transparency and high efficiency significantly reduced imminent security risks.

Challenge:
Administration of fileshare permissions

Solution:
Automation, self-service and approval processes
With go:Identity, IT now grants access to fileshares automatically based on the employee’s tasks. Users can request additional access in the go:Identity IT-Shop. The responsible persons approve them, and IT assigns them without any manual steps. Those responsible can now regularly check and correct authorizations. Any authorizations that are not needed are automatically withdrawn.

Challenge:Azure AD was out of the loop
An electronic parts manufacturer was struggling to integrate Azure AD into central business processes for managing accounts and permissions.

Solution:
Do not exclude cloud services
go:Identity established a secure bridge between the central applications and Azure AD, with real-time synchronization and high data consistency. Azure AD is now integrated despite its location in the cloud.

Challenge:Compliance audit passed only narrowly
A German financial institution did not fully pass a compliance audit and was facing stiff financial penalties. They found their employee access management was out of compliance. Reporting and attestation were missing as well.

Solution:Compliance achieved rapidly!
go:Identity consolidated all of the business applications for central permissions management, including attestation and reporting, into a central interface. By doing so, it successfully solved the abovementioned points.
Read the success Story
Functional benefits
-
Join / move/ leave of Identities
-
Automate on- and offboarding of employees
-
Self-service / Helpdesk
-
Request and approve of entitlements
-
Password management
-
Review the necessity of access authorizations
-
Ensure auditability (audit and compliance)
-
Recertify access rights and permissions
Technological benefits
-
Ready-made identity management system as an appliance
-
Pre-configured software – no complicated installation (virtual machine (VM))
-
Project-proven workflows and approval processes ready out of the box – can also be configured
-
Integration, go-live and operation on-prem
-
Multi language capability (DE, EN, FR – additional languages on demand)
Connectivity
-
Connection to standard systems, e.g. Microsoft Active Directory, MS Exchange, Notes, LDAP
-
SaaS systems, e.g. Microsoft Azure AD and Office 365, Salesforce, Workday, etc.
-
Business applications, e.g. SAP, Oracle, etc.
-
Databases: Oracle, MSSQL, MySQL, PostgreSQL etc.
-
Unix and Linux
-
Many other connectors
-
Custom integrations, including with customer applications, are simplified with a flexible connector framework
go:Identity Fileshare Info
Are you wondering what your users can effectively access on your NTFS-secured file servers?
go:Identity shows you fileshare permissions in the context of Identities by relating the NTFS permissions to the actual memberships in AD groups.
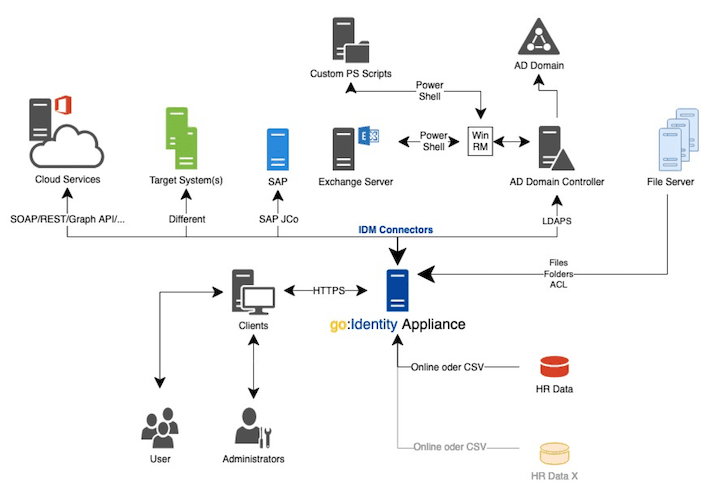
A typical go:Identity Landscape
Easy access
Ready-to-use integrations
Ready-made integration modules, known as IDM connectors, exist for a large number of system types.
Easy implementation
The prepared appliance is implemented in your environment in no time at all.
What is go:Identity SAM?
go:Identity Secure Access Module (SAM) adds an easy-to-implement access management component to go:Identity.
go:Identity SAM offers:
- Simple and contemporary authentication and authorization methods.
- Single sign-on (SSO) across systems and platforms.
- Multi-factor authentication (MFA).
- Modern authentication protocols (SAML, OAuth/OIDC).
go:Identity SAM technology:
go:Identity SAM is a ready-made software appliance:
- Simple integration into the existing environment.
- Cluster-capable for scalability and with high availability as needed.
- Standard protocols OpenID Connect and SAML 2.0.
- Multi-factor authentication (MFA, e.g. Google Authenticator or FreeOTP).
- Integration with existing directory services and Microsoft Active Directory.
- With application adapters and interfaces for easily integrating customers’ own applications using OIDC or SAML.
The seamless integration with go:Identity provides a comprehensive identity and access management solution. With a very short implementation time, it meets every standard for security, self-service, integration, automation and logging/compliance. In addition, it easily evolves to meet future challenges.
For instance, go:Identity can also be used to implement customer identity and access management (CIAM) scenarios.
Single sign-on (SSO)
SSO simplifies the sign-on process for users. The first step toward improvement is using a central service for authentication. Here, for instance, the central Active Directory is used as a reliable service to administer all of the authentication processes using the centrally managed “username/password” information. The users enter this information on a daily basis anyway, so they can easily remember it. If they forget it, they can reset and manage the password themselves through the self-service function in go:Identity. That makes things easier for the Helpdesk.
Federation
IT services are increasingly being used across organizations. That means external partners and customers need access to your organization’s infrastructure. Ideally, this should be a secure and simple process. The go:Identity Secure Access Module supports federation. It integrates external authentication services (ADFS, Ping Federate, Okta, etc.) in a secure, trustworthy way.
Multi-factor authentication (MFA)
If users are located outside the secure environment and need access to data, companies should ensure additional protection for this external access. MFA is an outstanding additional sign-on step. Today’s solutions are streamlined and easy to integrate. For instance, no parallel infrastructure needs to be implemented or hardware tokens distributed, etc.
By default, the go:Identity Secure Access Module supports integration of the Google Authenticator or FreeOTP. These are certified apps for smartphones that provide additional security for reviewing the sign-on request by the respective user.
That improves security overall: users are authenticated not just with something they know (password), but also with something they have (a smartphone app with a token).
Scenarios with go:Identity SAM
Users are always happy when IT can simplify the use of systems and applications. However, in most cases this simplification means a difficult balancing act between user-friendliness and security.
One security improvement is the integration of authentication for SSO via Active Directory using the universally accepted KERBEROS token, which is generated automatically during sign-on to the Active Directory and can continue to be used in the background. The token is used to suppress individual sign-on requests, which makes the process easier for users.
This method is an excellent way to grant users access to data within a secure infrastructure. In addition, such scenarios can be managed on a granular level using groups in the Active Directory. That way, users only receive the minimum access permission required, not the maximum permissions available. With the go:Identity basic edition, this takes place almost automatically.
By default, the go:Identity Secure Access Module supports Federation and SSO, which makes life easier for users as well as for IT managers.
Nowadays, the group of users who want to access a company’s systems and applications is no longer limited to its own employees.
Employees of partners, service providers or other external roles as well as potential customers often desire or need dedicated, controlled access. In order to simplify this management, the principle of “federation” has been established in recent years.
With corresponding trust settings from central authentication services of the individual organizations or general authentication services (e.g. PingOne, Okta, etc.), companies can allow selected users to access data without needing to manage the user accounts in their own system.
By default, the go:Identity Secure Access Module supports the currently accepted and generally used protocols SAML2 and OAuth/OIDC. Corresponding expansion packets can also be used to update proprietary applications so that the applications can support the protocols.
Nowadays, users also access critical data in unsecured and potentially risky situations (e.g. wi-fi in a café, airport or train). MFA minimizes the risk of unauthorized access and data loss.
It asks users to enter an additional feature besides the familiar username and password. This is normally a one-time password (OTP) provided as a numerical code. It is generated individually for the corresponding user, and is changed and double-checked on an ongoing basis, e.g. in the Google Authenticator.
The go:Identity Secure Access Module supports the Google Authenticator and FreeOTP as free versions.
Other products from COGNITUM Software
go:Roles
The comprehensive tool for entering, designing, controlling and maintaining business role models in Access Management - can be operated independently of the IAM system used.
Cognitum
The development platform for quick and easy creation of standardized and highly secure JAVA-based web applications.


